- 1. Implement the data link layer framing methods such as character, character stuffing and bit stuffing
- 2. Write a program to compute CRC code for the polynomials CRC-12, CRC-16 and CRC CCIP
- 3. Develop a simple data link layer that performs the flow control using the sliding window protocol, and loss recovery using the Go-Back-N mechanism.
- 4. Implement Dijsktra’s algorithm to compute the shortest path through a network
- 5. Take an example subnet of hosts and obtain a broadcast tree for the subnet
- 6. Implement distance vector routing algorithm for obtaining routing tables at each node
- 7. Implement data encryption and data decryption
- 8. Write a program for congestion control using Leaky bucket algorithm
- 9. Write a program for frame sorting technique used in buffers
- 11. How to run Nmap scan
- 12. Operating System Detection using Nmap
-
13. Do the following using NS2 Simulator
i. NS2 Simulator-Introduction
ii. Simulate to Find the Number of Packets Dropped
iii. Simulate to Find the Number of Packets Dropped by TCP/UDP
iv. Simulate to Find the Number of Packets Dropped due to Congestion
v. Simulate to Compare Data Rate& Throughput.
vi. Simulate to Plot Congestion for Different Source/Destination
vii. Simulate to Determine the Performance with respect to Transmission of Packets
AIM: Wireshark
- i. Packet Capture Using Wire shark
- ii. Starting Wire shark
- iii. Viewing Captured Traffic
- iv. Analysis and Statistics & Filters Viewing CapturedTraffic
- v. Analysis and Statistics & Filters.
Theory:
Wireshark-win64-3.4.3)
Wireshark is a network packet analyzer. A network packet analyzer presents captured packet data in as much detail as possible.
You could think of a network packet analyzer as a measuring device for examining what’s happening inside a network cable, just like an electrician uses a voltmeter for examining what’s happening inside an electric cable (but at a higher level, of course).
Here are some reasons people use Wireshark:
Network administrators use it to troubleshoot network problems Network security engineers use it to examine security problems QA engineers use it to verify network applications
Developers use it to debug protocol implementations
People use it to learn network protocol internals
i) packet capture using click capture:
 Click the red “Stop” button near the top left corner of the window when you want to stop capturing traffic
Click the red “Stop” button near the top left corner of the window when you want to stop capturing traffic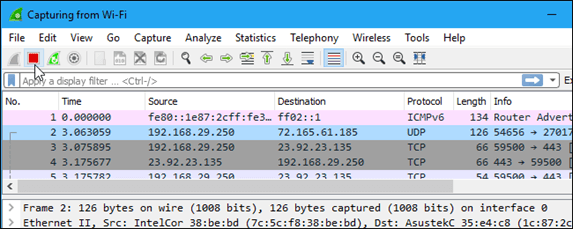
ii) starting wire shark
After downloading and installing Wireshark, you can launch it and double-click the name of a network interface under Capture to start capturing packets on that interface(wifi or Ethernet or LAN)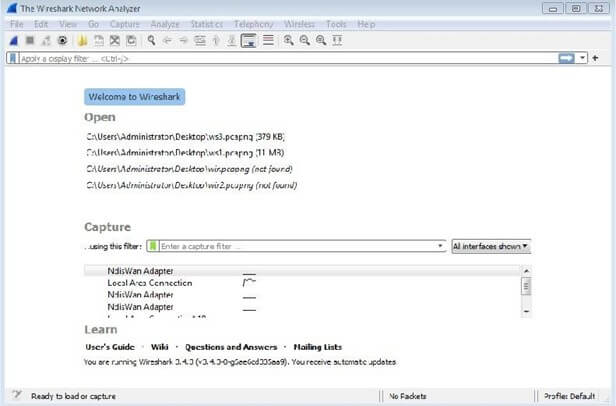
iii) Viewing captired Traffic
View > Coloring Rules.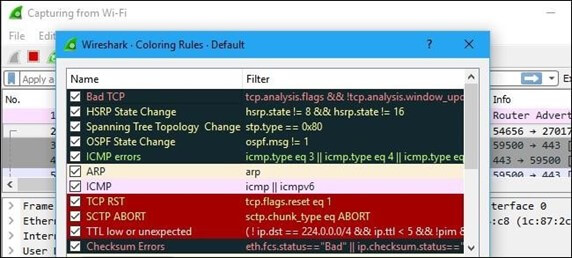
You can also save your own captures in Wireshark and open them later. Click File > Save to save your captured packets.
iv) Analysis and Statistics and Filters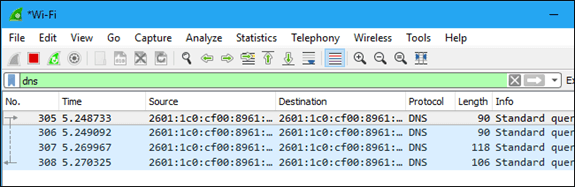
Apply a filter by typing it into the filter box at the top of the window and clicking Apply (or pressing Enter). For example, type “dns” and you’ll see only DNS packets. When you start typing, Wireshark will help you autocomplete your filter. To analyze traffic,
click Analyze > Display Filters to choose a filter from among the default filters included inWireshark.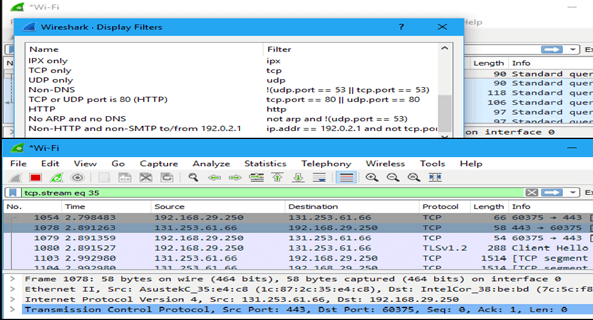
v) To find Statistics:
Goto to statistics and select Protocol(DHCP, UDP Multicast)