Using Cookies and Session for Session Tracking in Web Applications
In the inherently stateless world of HTTP, maintaining user identity and state across multiple requests is a critical challenge. Session tracking provides the solution, allowing web applications to remember a user as they navigate different pages or interact over time. Two primary mechanisms facilitate session tracking: HTTP cookies and the server-side HttpSession object. Understanding how to use cookies and session for session tracking is fundamental for building personalized and interactive web experiences.
Understanding Session Tracking
HTTP is a stateless protocol, meaning that each request from a client to a server is treated independently, without any memory of previous requests. Consequently, for applications that require maintaining a user’s logged-in status, shopping cart contents, or personalized settings across multiple page views, this stateless nature poses a significant hurdle. Session tracking is the technique used to overcome this limitation. It ensures that the web server can identify a series of related requests from the same user as part of a single, ongoing interaction, effectively creating a “session.”
Session Tracking with Cookies
One of the most common and oldest methods for session tracking involves using HTTP cookies. Cookies are small pieces of data that a server sends to a user’s web browser, and the browser then stores them. Subsequently, the browser sends these cookies back to the same server with every subsequent request.
What are Cookies?
A cookie is a small text file that a web server embeds on the user’s hard drive via their browser. These files contain specific information, typically a unique identifier. This identifier allows the server to recognize the user during subsequent visits. Cookies are generally used to store small amounts of data that help personalize user experiences, such as user preferences or, critically, a session ID for session tracking.
How Cookies Work for Session Tracking
The process of using cookies for session tracking typically unfolds as follows:
- First Request: A user makes an initial request to a web application.
- Server Generates Session ID: The server, perhaps a JSP or Servlet, generates a unique session ID for this new user.
- Server Sends Cookie: The server then sends this session ID back to the user’s browser within an HTTP
Set-Cookieresponse header. - Browser Stores Cookie: The browser stores this cookie on the client’s machine.
- Subsequent Requests: For all subsequent requests to the same domain, the browser automatically includes the cookie (with the session ID) in the HTTP
Cookierequest header. - Server Recognizes User: The server reads this session ID from the incoming cookie and uses it to identify the user and retrieve any associated session data.
Here is a basic example of how to set and retrieve a cookie in JSP:
<%
// Setting a cookie
Cookie userCookie = new Cookie("username", "JSPUser123");
userCookie.setMaxAge(60 * 60 * 24); // Cookie valid for 24 hours
response.addCookie(userCookie);
// Retrieving a cookie
String storedUsername = "Guest";
Cookie[] cookies = request.getCookies();
if (cookies != null) {
for (Cookie cookie : cookies) {
if ("username".equals(cookie.getName())) {
storedUsername = cookie.getValue();
break;
}
}
}
%>
<p>Hello, <%= storedUsername %>!</p>
Types of Cookies for Session Tracking
When using cookies for session tracking, two main types are relevant:
- Session Cookies: These cookies are temporary. They are stored in the browser’s memory and are deleted automatically when the user closes their browser. They are commonly used to store the session ID for a single Browse session.
- Persistent Cookies: These cookies are stored on the user’s hard drive and remain there until their expiration date or until the user manually deletes them. They are suitable for “Remember Me” functionalities but are less common for basic session ID storage due to security and privacy concerns.
Security is paramount when using cookies. Employing HttpOnly flags prevents client-side scripts from accessing cookies, mitigating Cross-Site Scripting (XSS) risks. Additionally, using Secure flags ensures cookies are only sent over HTTPS. SameSite attributes also enhance protection against Cross-Site Request Forgery (CSRF).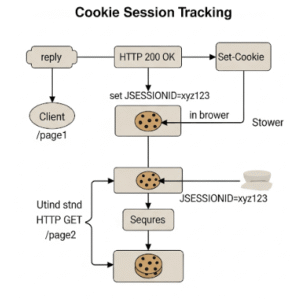
Session Tracking with HttpSession (Server-Side Session)
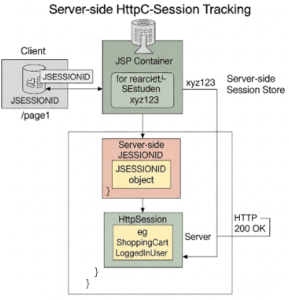
While cookies handle the identification of a user, the actual storage of larger, more sensitive user-specific data for session tracking typically occurs on the server side using the HttpSession object. This server-side session relies on a unique session ID, often passed via a cookie.
What is HttpSession?
The HttpSession object is a server-side object that allows a web application to store information about a user’s session. Each user who interacts with the application typically gets a unique HttpSession instance. This object acts as a temporary data store, holding user-specific data that needs to persist across multiple requests within that single session. For example, a user’s shopping cart or login status can be stored in the session.
How HttpSession Works for Session Tracking
The lifecycle of an HttpSession for session tracking involves several steps:
- Session Creation: When a user first accesses an application that uses sessions (or when the application explicitly calls
request.getSession()), the web container creates a newHttpSessionobject. It then generates a unique session ID for it. - Session ID Transmission: This session ID is usually sent to the client’s browser as a session cookie (e.g.,
JSESSIONID). If cookies are disabled, URL rewriting can be used, where the session ID is appended to all URLs. - Data Storage and Retrieval: Developers can store various objects as attributes in the
HttpSessionusingsession.setAttribute("key", value)and retrieve them usingsession.getAttribute("key"). - Session Invalidation: A session remains active until it is explicitly invalidated (e.g.,
session.invalidate()), or until a configured inactivity timeout occurs.
Here’s a simple JSP example demonstrating HttpSession:
<%
// Get the current session, create if one doesn't exist
HttpSession currentSession = request.getSession();
// Increment a visit counter for this session
Integer visitCount = (Integer) currentSession.getAttribute("visitCount");
if (visitCount == null) {
visitCount = 1;
} else {
visitCount++;
}
currentSession.setAttribute("visitCount", visitCount);
%>
<p>You have visited this page <%= visitCount %> times in this session.</p>
<p>Your session ID is: <%= currentSession.getId() %></p>
Advantages and Disadvantages of HttpSession
Using HttpSession for session tracking offers several benefits:
- Security: Sensitive data is stored on the server, not exposed to the client, making it more secure.
- Data Size: It can store a large amount of data compared to cookies, which have size limitations.
- Server-Side Control: The server manages the session lifecycle and data, providing greater control.
However, there are also some drawbacks:
- Server Memory Usage: Storing session data for many active users can consume significant server memory.
- Scalability Challenges: In distributed environments with multiple servers (e.g., load balancing), ensuring “sticky sessions” (where a user always hits the same server) or session replication is crucial.
Comparing Cookies and HttpSession for Session Tracking
Both cookies and HttpSession are integral to session tracking, yet they operate differently and are often used in conjunction. Here’s a comparison:
| Feature | HTTP Cookies | HttpSession (Server-Side Session) |
|---|---|---|
| Storage Location | Client’s browser | Server’s memory/disk (managed by container) |
| Data Visibility | Exposed to client (can be seen/tampered) | Not exposed to client (more secure) |
| Data Size Limit | Small (typically ~4KB per cookie) | Larger (limited by server memory) |
| Primary Role | Storing session ID; client-side preferences | Storing user-specific data; managing user state on server |
| Persistence | Session-based (browser close) or persistent | Session-based (inactivity timeout or invalidate) |
| Server Load | Low (data on client) | Higher (consumes server memory) |
| Security Risk | XSS, CSRF, cookie hijacking | Server memory exhaustion, session hijacking (if ID stolen) |
Ultimately, a common practice is to use a session cookie to store the unique JSESSIONID, which then serves as the key to retrieve the corresponding, more substantial HttpSession object and its data on the server.
Best Practices for Session Tracking
Effective session tracking extends beyond mere implementation; it demands adherence to best practices for security and performance:
- Security for Cookies: Always use
HttpOnlyandSecureflags for session cookies. TheHttpOnlyflag prevents client-side scripts from accessing the cookie, thereby mitigating XSS attacks. TheSecureflag ensures cookies are only sent over encrypted (HTTPS) connections. Furthermore, implementing theSameSiteattribute can help protect against CSRF attacks. - Session Timeout Management: Configure appropriate session timeouts. Setting them too long can increase the risk of session hijacking, while setting them too short can frustrate users by forcing frequent re-logins. Invalidate sessions explicitly upon user logout.
- Avoid Storing Sensitive Data in Cookies: Never store sensitive personal information or critical application data directly in client-side cookies. Instead, store such data in the
HttpSessionobject on the server and use the cookie only for the session ID. - Regularly Review Session Management: Periodically review your application’s session tracking mechanisms for potential vulnerabilities. Keep up-to-date with security recommendations for your web server and application framework.
By diligently applying these practices, you can create robust and secure web applications that effectively manage user state.
For detailed information on HTTP cookies and their attributes, refer to the MDN Web Docs on HTTP Cookies.
