- Metrics for Process and Products
- Software measurement
- Metrics for Software Quality
- Risk Management
- Reactive versus Proactive Risk Strategies
- Software Risks
- Risk Identification
- Risk Projection
- Risk Refinement
- RMMM
- RMMM Plan
- Quality Management
- Quality Concepts
- Software Reviews
- Formal Technical Reviews
- Statistical Software Quality Assurance
- Software Reliability
- The ISO 9000 Quality Standards
Introduction to Risk Identification
Within the broader discipline of risk management, risk identification is the critical initial step. It involves systematically specifying potential threats to the project plan and the software product. The primary goal of this phase is to uncover possible problems that could negatively impact the software development process or the final outcome. By identifying risks early, project teams can anticipate challenges, prepare appropriate responses, and proactively minimize their potential negative consequences before they materialize into actual issues. This proactive approach is fundamental for successful project execution.
Approaches to Risk Identification
Risk identification can be performed using two primary approaches, ensuring comprehensive coverage of potential threats:
Generic Risk Identification
This approach focuses on identifying potential threats that are applicable to any software project, regardless of its specific details. It involves considering common risks that frequently arise across various development efforts. These general risks often include issues related to budget, schedule, or personnel.
Product-Specific Risk Identification
Conversely, this approach delves into uncovering threats that are unique to the particular software product being developed. It requires a deep understanding of the specific people involved, the technologies used, and the operational environment in which the product will function. This detailed examination helps pinpoint tailored risks that might not be apparent in a generic analysis.
Steps in Risk Identification
Risk identification is typically a systematic process, often led by the project manager, and involves a series of structured steps to ensure thoroughness.
Step 1: Preparation of Risk Item Checklist
The first step involves creating a comprehensive checklist of potential risk items. These items are identified by considering known and predictable components relevant to the project. Key areas to assess when building this checklist include:
- Product Size: Risks related to the sheer scale and complexity of the software product being developed.
- Business Impact: Risks associated with how the software might affect the market or management’s strategic goals.
- Customer Characteristics: Threats arising from the nature of the customer, such as unclear communication or changing expectations.
- Process Definition: Risks inherent in the chosen software development process itself, like inefficiencies or ambiguities in workflows.
- Development Environment: Threats linked to the tools, infrastructure, and overall technological environment used for development.
- Staff Size and Experience: Risks related to having an insufficient number of skilled or experienced personnel on the team.
- Technology to be Built: Understanding the complexity of the system and identifying risks related to adopting new or unproven technologies.
Step 2: Creating Risk Components & Drivers List
Following the checklist, the next step involves preparing a set of risk components and their associated drivers. This detailed list helps in analyzing the probability of each risk’s occurrence and its potential impact on the project. Guidelines from sources like the Air Force have been developed to aid in this structured identification of components and their contributing factors.
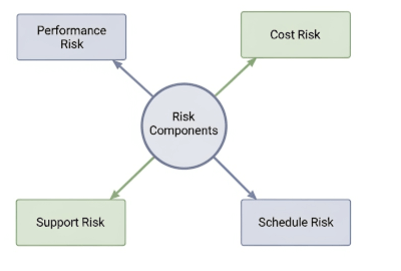
Types of Risk Components
Specific risk components are frequently considered during the identification phase, providing a framework for analyzing the nature of the threat:
- Performance Risk: This measures the degree of uncertainty that the software product will actually satisfy its specified functional and non-functional requirements. It questions whether the system will perform as expected under various conditions.
- Cost Risk: This component refers to the degree of uncertainty that the software project will maintain its allocated budget. It focuses on the potential for financial overruns due to various factors.
- Support Risk: This indicates the degree of uncertainty that the software product will be easy to correct, modify, or adapt after deployment. It directly relates to the long-term maintainability and evolution of the software.
- Schedule Risk: This assesses the degree of uncertainty that the software project will maintain its planned schedule and be delivered on time. It focuses on potential delays that could impact the project timeline.
Assessing Overall Project Risk
To gain a comprehensive understanding of the overall project risk, several key questions can be asked during the identification process. These questions act as prompts to uncover areas of potential vulnerability:
- Will the project receive proper support from the customer’s management?
- Are the end-users genuinely committed to the software being produced?
- Is there a clear and unambiguous understanding of all project requirements?
- Is the customer actively involved in the definition and refinement of requirements?
- Are the expectations for the final product realistic and achievable?
- Is the project scope stable, or is it prone to frequent changes?
- Are there team members with all the necessary required skills and expertise?
- Are the project requirements truly stable and unlikely to change significantly?
- Is the technology used for the software known and familiar to the developers?
- Is the size of the development team sufficient to build the required product effectively?
- Are all stakeholders, including customers, fully aware of the importance of the product and the system’s requirements?
These questions help identify areas where uncertainty or lack of clarity might translate into significant project risks.
Conclusion
Risk identification forms the bedrock of effective risk management in software engineering. By systematically identifying both generic and product-specific threats, and by understanding various risk components like performance, cost, support, and schedule risks, project teams can proactively prepare for challenges. This early and comprehensive identification process, supported by checklists and critical questioning, significantly enhances a project’s ability to maintain its trajectory, manage resources effectively, and ultimately deliver a high-quality software product within defined constraints.
