Menu
- 1. Implement the data link layer framing methods such as character, character stuffing and bit stuffing
- 2. Write a program to compute CRC code for the polynomials CRC-12, CRC-16 and CRC CCIP
- 3. Develop a simple data link layer that performs the flow control using the sliding window protocol, and loss recovery using the Go-Back-N mechanism.
- 4. Implement Dijsktra’s algorithm to compute the shortest path through a network
- 5. Take an example subnet of hosts and obtain a broadcast tree for the subnet
- 6. Implement distance vector routing algorithm for obtaining routing tables at each node
- 7. Implement data encryption and data decryption
- 8. Write a program for congestion control using Leaky bucket algorithm
- 9. Write a program for frame sorting technique used in buffers
-
10. Wireshark
i. Packet Capture Using Wire shark
ii. Starting Wire shark
iii. Viewing Captured Traffic
iv. Analysis and Statistics & Filters - 11. How to run Nmap scan
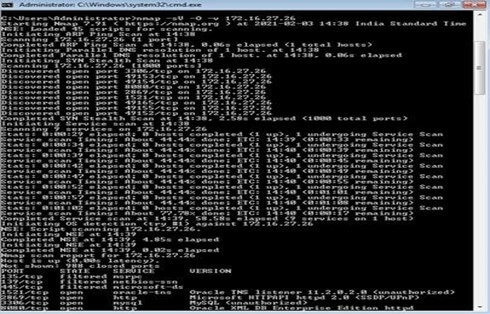
AIM:Operating system detection using NMAP
Theory:
- To detect OS use the command:
- Goto Command Prompt
- Type nmap
- Type: nmap -sV -O 172.16.27.26