- 1. Implement the data link layer framing methods such as character, character stuffing and bit stuffing
- 2. Write a program to compute CRC code for the polynomials CRC-12, CRC-16 and CRC CCIP
- 3. Develop a simple data link layer that performs the flow control using the sliding window protocol, and loss recovery using the Go-Back-N mechanism.
- 4. Implement Dijsktra’s algorithm to compute the shortest path through a network
- 5. Take an example subnet of hosts and obtain a broadcast tree for the subnet
- 6. Implement distance vector routing algorithm for obtaining routing tables at each node
- 7. Implement data encryption and data decryption
- 9. Write a program for frame sorting technique used in buffers
-
10. Wireshark
i. Packet Capture Using Wire shark
ii. Starting Wire shark
iii. Viewing Captured Traffic
iv. Analysis and Statistics & Filters - 11. How to run Nmap scan
- 12. Operating System Detection using Nmap
-
13. Do the following using NS2 Simulator
i. NS2 Simulator-Introduction
ii. Simulate to Find the Number of Packets Dropped
iii. Simulate to Find the Number of Packets Dropped by TCP/UDP
iv. Simulate to Find the Number of Packets Dropped due to Congestion
v. Simulate to Compare Data Rate& Throughput.
vi. Simulate to Plot Congestion for Different Source/Destination
vii. Simulate to Determine the Performance with respect to Transmission of Packets
Aim: write a program for congestion control using leaky bucket algorithm
Theory:
The congesting control algorithms are basically divided into two groups: open loop and closed loop. Open loop solutions attempt to solve the problem by good design, in essence, to make sure it does not occur in the first place. Once the system is up and running, midcourse corrections are not made. Open loop algorithms are further divided into ones that act at source versus ones that act at the destination.
In contrast, closed loop solutions are based on the concept of a feedback loop if there is any congestion. Closed loop algorithms are also divided into two sub categories: explicit feedback and implicit feedback. In explicit feedback algorithms, packets are sent back from the point of congestion to warn the source. In implicit algorithm, the source deduces the existence of congestion by making local observation, such as the time needed for acknowledgment to come back.
words, if one or more process are already queued, the new packet is unceremoniously discarded. This arrangement can be built into the hardware interface or simulate d by the host operating system. In fact it is nothing other than a single server queuing system with constant service time.
The host is allowed to put one packet per clock tick onto the network. This mechanism turns an uneven flow of packet from the user process inside the host into an even flow of packet onto the network, smoothing out bursts and greatly reducing the chances of congestion
The presence of congestion means that the load is (temporarily) greater than the resources (in part of the system) can handle. For subnets that use virtual circuits internally, these methods can be used at the network layer.
Another open loop method to help manage congestion is forcing the packet to be transmitted at a more predictable rate. This approach to congestion management is widely used in ATM networks and is called traffic shaping.
The other method is the leaky bucket algorithm. Each host is connected to the network by an interface containing a leaky bucket, that is, a finite internal queue. If a packet arrives at the queue when it is full, the packet is discarded. In other
ALGORITHM/FLOWCHART:
Step 1: Start
Step 2: Set the bucket size or the buffer size
Step3: Set the output rate.
Step 4: Transmit the packets such that there is no overflow.
Step 5: Repeat the process of transmission until all packets are transmitted. (Reject packets where its size is greater than the bucket size)
Step 6: Stop
SOURCE CODE:
#include<stdio.h>
#include<stdlib.h>
#include<unistd.h>
#define NOF_PACKETS 10
intrand(int a)
{
intrn = (random() % 10) % a;
returnrn == 0 ? 1 :rn;
}
intmain()
{
intpacket_sz[NOF_PACKETS], i, clk, b_size, o_rate, p_sz_rm=0, p_sz, p_time, op;
for(i = 0; i<NOF_PACKETS; ++i)
packet_sz[i] = rand(6) * 10;
for(i = 0; i<NOF_PACKETS; ++i)
printf(“\npacket[%d]:%d bytes\t”, i, packet_sz[i]);
printf(“\nEnter the Output rate:”);
scanf(“%d”, &o_rate);
printf(“Enter the Bucket Size:”);
scanf(“%d”, &b_size);
for(i = 0; i<NOF_PACKETS; ++i)
{
if( (packet_sz[i] + p_sz_rm) >b_size)
if(packet_sz[i] >b_size)/*compare the packet siz with bucket size*/
printf(“\n\nIncoming packet size (%dbytes) is Greater than bucket capacity (%dbytes)-PACKET REJECTED”, packet_sz[i], b_size);
else
printf(“\n\nBucket capacity exceeded-PACKETS REJECTED!!”); else
{
p_sz_rm += packet_sz[i];
printf(“\n\nIncoming Packet size: %d”, packet_sz[i]); printf(“\nBytes remaining to Transmit: %d”, p_sz_rm); p_time = rand(4) * 10;
printf(“\nTime left for transmission: %d units”, p_time); for(clk = 10; clk<= p_time; clk += 10)
{
sleep(1); if(p_sz_rm)
{
if(p_sz_rm<= o_rate)/*packet size remaining comparing with output rate*/
op = p_sz_rm, p_sz_rm = 0; else
op = o_rate, p_sz_rm -= o_rate; printf(“\nPacket of size %d Transmitted”, op);
printf(“—- Bytes Remaining to Transmit: %d”, p_sz_rm);
}
else
{
printf(“\nTime left for transmission: %d units”, p_time-clk); printf(“\nNo packets to transmit!!”);
}
}
}
}
}
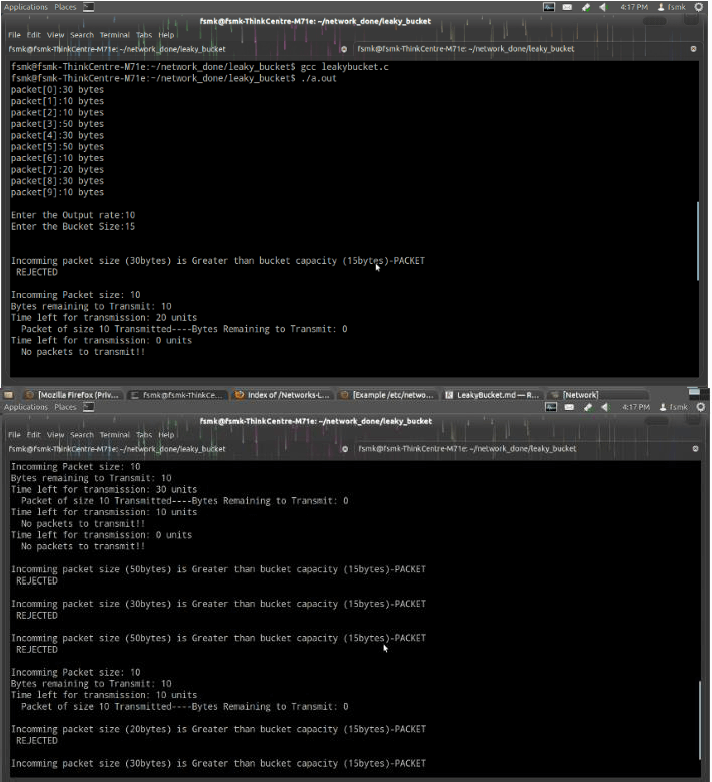
Output: