- 1. Implement the data link layer framing methods such as character, character stuffing and bit stuffing
- 2. Write a program to compute CRC code for the polynomials CRC-12, CRC-16 and CRC CCIP
- 3. Develop a simple data link layer that performs the flow control using the sliding window protocol, and loss recovery using the Go-Back-N mechanism.
- 4. Implement Dijsktra’s algorithm to compute the shortest path through a network
- 5. Take an example subnet of hosts and obtain a broadcast tree for the subnet
- 6. Implement distance vector routing algorithm for obtaining routing tables at each node
- 8. Write a program for congestion control using Leaky bucket algorithm
- 9. Write a program for frame sorting technique used in buffers
-
10. Wireshark
i. Packet Capture Using Wire shark
ii. Starting Wire shark
iii. Viewing Captured Traffic
iv. Analysis and Statistics & Filters - 11. How to run Nmap scan
- 12. Operating System Detection using Nmap
-
13. Do the following using NS2 Simulator
i. NS2 Simulator-Introduction
ii. Simulate to Find the Number of Packets Dropped
iii. Simulate to Find the Number of Packets Dropped by TCP/UDP
iv. Simulate to Find the Number of Packets Dropped due to Congestion
v. Simulate to Compare Data Rate& Throughput.
vi. Simulate to Plot Congestion for Different Source/Destination
vii. Simulate to Determine the Performance with respect to Transmission of Packets
AIM: Implement data encryption and data decryption.
Theory:
Data encryption standard was widely adopted by the industry in security products. Plain text is encrypted in blocks of 64 bits yielding 64 bits of cipher text. The algorithm which is parameterized by a 56 bit key has 19 distinct stages. The first stage is a key independent transposition and the last stage is exactly inverse of the transposition. The remaining stages are functionally identical but are parameterized by different functions of the key. The algorithm has been designed to allow decryption to be done with the same key as encryption
Program:
#include<stdio.h>
#include<string.h>
#include<ctype.h>
void main()
{
char pwd[20];
char alpha[26]=”abcdefghijklmnopqrstuvwxyz”;
int num[20],i,n,key;
printf(“\nEnter the password:”);
scanf(“%s”,&pwd);
n=strlen(pwd);
for(i=0;i<n;i++)
num[i]=toascii(tolower(pwd[i]))-‘a’;
printf(“\nEnter the key:”);
scanf(“%d”,&key);
for(i=0;i<n;i++)
num[i]=(num[i]+key)%26;
for(i=0;i<n;i++)
pwd[i]=alpha[num[i]];
printf(“\nThe key is:%d”,key);
printf(“\nEncrypted text is:%s”,pwd);
for(i=0;i<n;i++)
{
num[i]=(num[i]-key)%26;
if(num[i]<0)
num[i]=26+num[i];
pwd[i]=alpha[num[i]];
}
printf(“\nDecrypted text is:%s”,pwd);
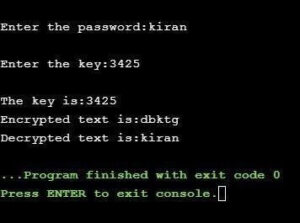
Output: