Elements of Transport Protocols
Transport protocols are essential for ensuring reliable communication between applications over a network. They manage various aspects of data transmission, including error control, sequencing, flow control, and connection management. This article explores the key elements of transport protocols, highlighting their similarities and differences with data link protocols, addressing mechanisms, connection establishment and release, error control, flow control, multiplexing, and crash recovery.
1. Overview of Transport Protocols
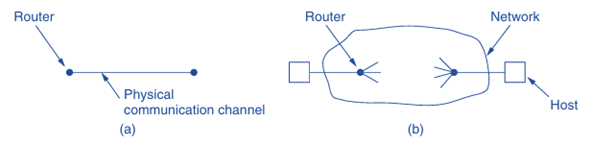
Transport protocols operate between two transport entities, facilitating communication across an entire network rather than just a physical link. Unlike data link protocols, which manage communication over point-to-point links, transport protocols must handle the complexities of a broader network environment. This includes addressing, connection management, and ensuring data integrity despite potential issues like packet loss, duplication, and delays.
Key Differences from Data Link Protocols
→ Communication Environment: Data link protocols operate over direct physical channels, while transport protocols function over the entire network.
→ Addressing: Transport protocols require explicit addressing of destinations, whereas data link protocols do not.
→ Connection Establishment: Establishing a connection in transport protocols is more complex due to the potential for packet loss and delays.
→ Storage Capacity: Transport protocols must account for the possibility of packets being delayed or duplicated within the network.
2. Addressing in Transport Protocols
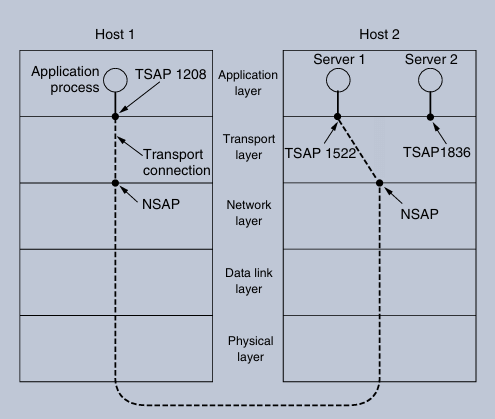
When an application process wants to establish a connection, it must specify the destination transport service access point (TSAP). In the Internet, these endpoints are referred to as ports. The transport layer uses TSAPs to distinguish between multiple transport endpoints that may share the same network service access point (NSAP).
Transport Service Access Points (TSAPs)
→ Definition: TSAPs are specific endpoints in the transport layer where application processes can listen for connection requests.
→ Network Service Access Points (NSAPs): These are analogous to TSAPs at the network layer, with IP addresses serving as examples of NSAPs.
3. Connection Establishment
Establishing a connection in transport protocols involves a series of steps to ensure reliability. The process is more complicated than simply sending a connection request due to potential issues like packet loss and duplication.
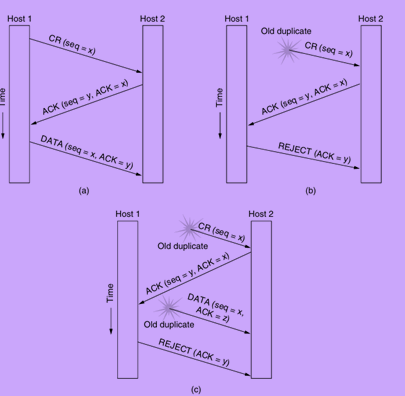
The Three-Way Handshake
The three-way handshake is a common method for establishing a connection:
1.Connection Request: The initiating host sends a connection request with a chosen sequence number.
2.Acknowledgment: The receiving host acknowledges the request and sends back its own initial sequence number.
3.Final Acknowledgment: The initiating host acknowledges the receiving host’s sequence number in the first data segment it sends.
This method helps prevent issues with delayed duplicate packets, ensuring that only current connection requests are processed.
4. Connection Release
Releasing a connection can be as complex as establishing one. There are two primary styles of connection termination: asymmetric and symmetric release.
Asymmetric vs. Symmetric Release
→ Asymmetric Release: Similar to a telephone call, where one party can hang up and terminate the connection abruptly, potentially leading to data loss.
→ Symmetric Release: Each direction of the connection is released independently, allowing for a more graceful termination without data loss.
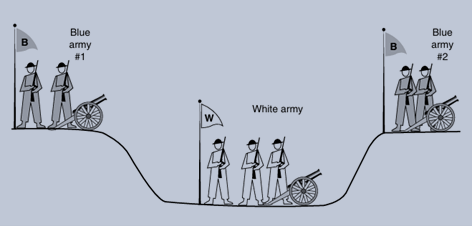
The Two-Army Problem
The two-army problem illustrates the challenges of ensuring both parties agree to disconnect. If neither side is prepared to disconnect until it is convinced the other side is ready, the disconnection may never occur. To avoid this, transport protocols often allow each side to independently decide when to terminate the connection.
5. Error Control and Flow Control
Transport protocols must ensure that data is delivered reliably and efficiently. This involves two key mechanisms: error control and flow control.
Error Control
Error control ensures that data is delivered without errors. Common techniques include:
→ Checksums: Used to verify the integrity of data segments.
→ Automatic Repeat reQuest (ARQ): Segments are retransmitted until acknowledged by the receiver.
Flow Control
Flow control prevents a fast sender from overwhelming a slow receiver. Techniques include:
→ Sliding Window Protocol: Allows multiple segments to be in transit before requiring an acknowledgment, improving efficiency.
6. Multiplexing
Multiplexing allows multiple transport connections to share a single network address. This is crucial when a host has limited network addresses or when multiple connections need to be managed simultaneously.
Types of Multiplexing
→ Standard Multiplexing: Multiple transport connections use the same network address, requiring the transport layer to determine which process should receive incoming segments.
→ Inverse Multiplexing: Distributes traffic across multiple network paths to increase bandwidth and reliability. Protocols like SCTP (Stream Control Transmission Protocol) utilize this method to enhance performance.
7. Crash Recovery
Crash recovery is vital for maintaining the integrity of transport protocols, especially in long-lived connections. When a host crashes, it may lose track of its state, complicating recovery efforts.
Recovery Strategies
→ Broadcast Recovery: Upon reboot, a server can broadcast a request for clients to report the status of open connections. However, this method can lead to inconsistencies if acknowledgments are lost.
→ End-to-End Acknowledgment: Ensures that the transport layer can recover from failures, but it requires higher layers to maintain enough state information to reconstruct the previous state.
Challenges in Recovery
The inability to achieve true end-to-end acknowledgment complicates recovery. For instance, if a client receives an acknowledgment but the server crashes before processing the request, the client may incorrectly assume the operation was successful.
Conclusion
Understanding the elements of transport protocols is crucial for ensuring reliable and efficient communication over networks. By managing addressing, connection establishment and release, error and flow control, multiplexing, and crash recovery, transport protocols provide a robust framework for application-layer communication. As networks continue to evolve, the importance of these protocols in maintaining data integrity and performance cannot be overstated.
By focusing on these key elements, developers and network engineers can design systems that effectively handle the complexities of modern network communication.
